Get your free eGuide
10 Steps to Avoid Breaches and Data Leaks in Office 365
10 Steps to Avoid Breaches and Data Leaks in Office 365




Octiga has transformed how we assist our Office 365 dependent clients. Now, we can monitor and react to risky activity and report and remediate for best practice configurations tailored to each client's unique business.
It just works. This is a game-changer for us. It has helped us close the gaps where security breaches can occur for our clients. It has saved me so much stress and time. Everyone should be using it.

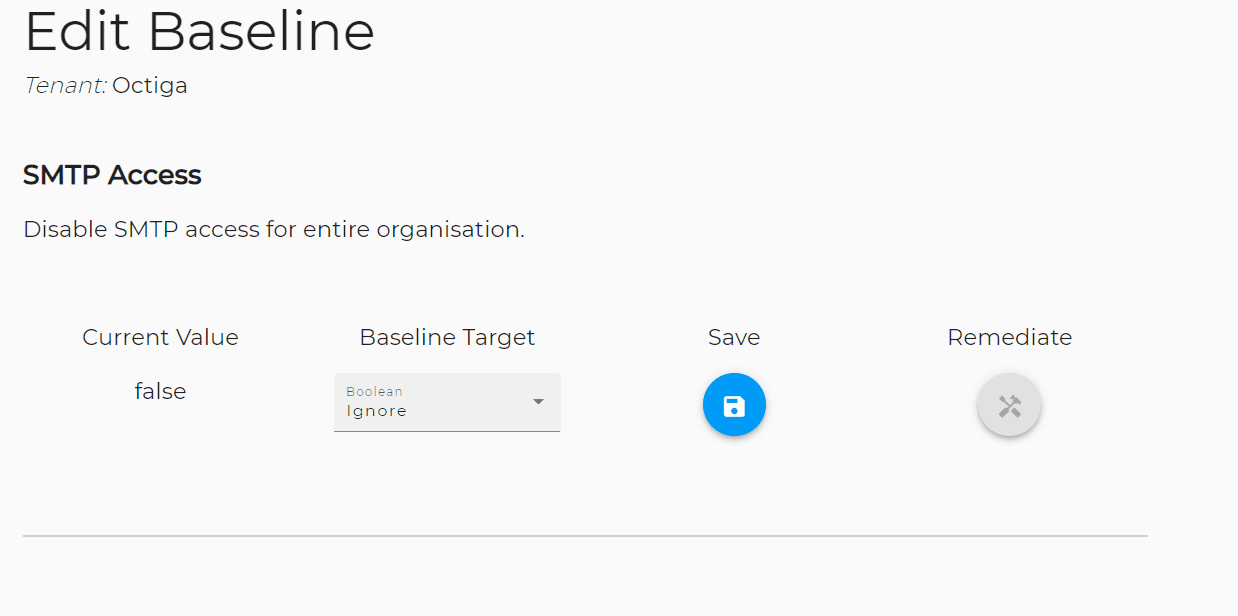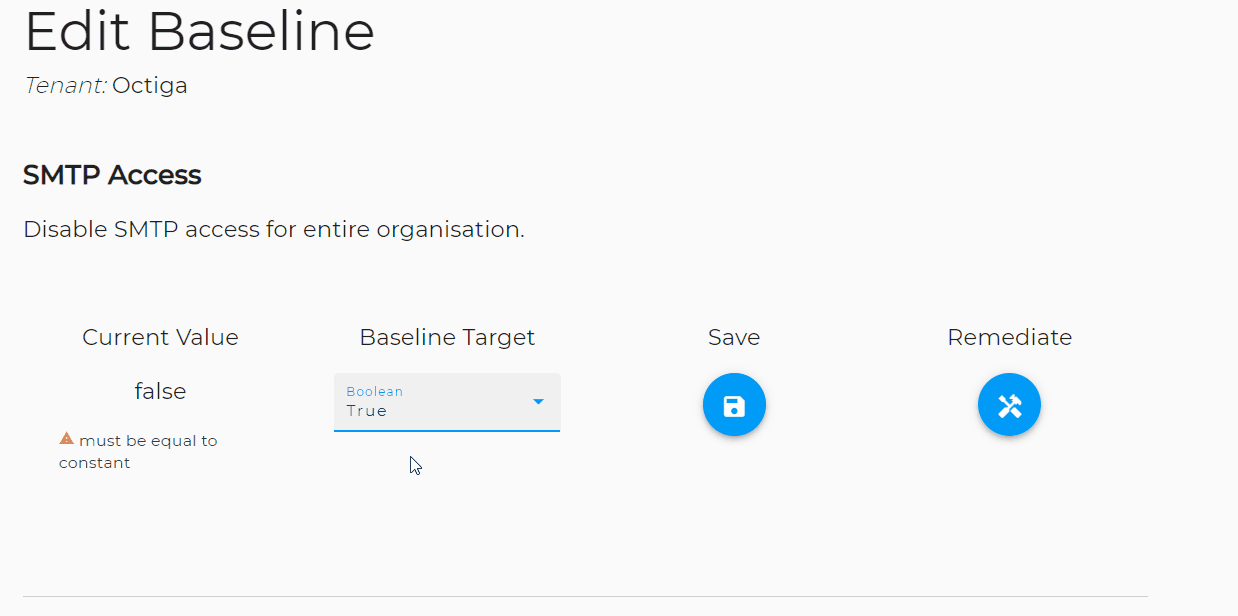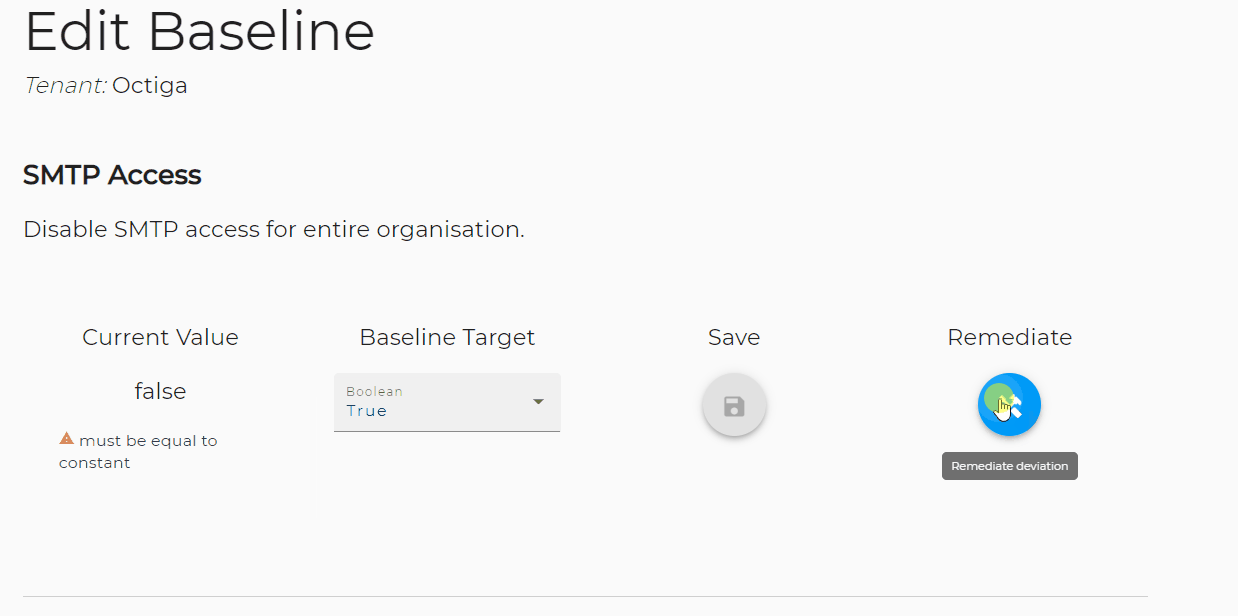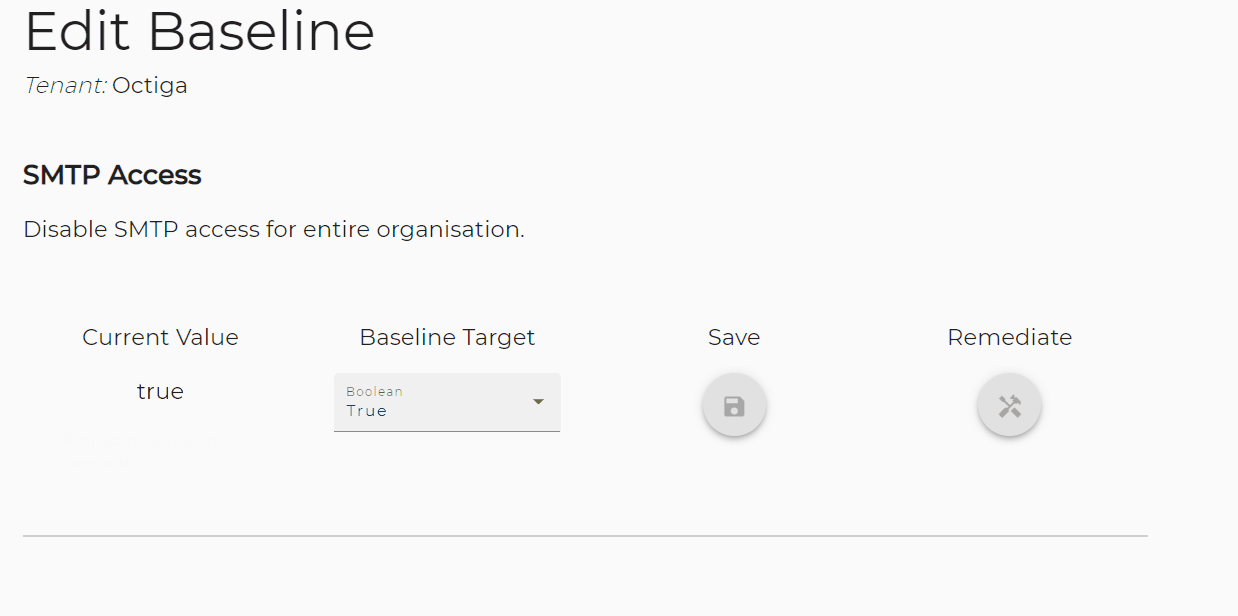















Microsoft's security team has recently made a significant discovery regarding an increase in cyber-attacks orchestrated by the Russian state-backed group known as the Midnight Blizzard crew. This group, which also operates under the aliases Nobelium, APT29, Cozy Bear, Iron Hemlock, and The Dukes, has been actively targeting personal credentials, according to Microsoft's findings.
Read Story
Discover the limitations of the M365 Secure Score for MSPs. Understand the scope and potential restrictions when using this tool to assess and enhance the security posture of Microsoft 365 environments. Know how to navigate through these shortcomings.
Read Story
The purpose of the Octiga Office 365 security app is not to replace M365 security but to ensure that MSPs can deliver it consistently, coherently and rapidly to all your clients. A short video explains how Octiga makes MSPs' work super efficient and super fast.
Read Story
Drill into some of the major Office365 auditing challenges that MSPs face and understand the constituents of an effective Office365 auditing solution to improve business.
Read Story
Despite the tight security services provided by Microsoft, SMEs' Office 365 is breached intentionally by malicious actors or inadvertently by insiders. Follow these SharePoint Online Security Best Practices to protect your organisation & employees from common security mistakes in 2022.
Read Story
The advantages of SIEM make it a go-to tool for Office 365 security; however, the long list of implementation pitfalls can sometimes exceed its benefits. Here are some insights on why MSPs need to reconsider Office 365 SIEM and how they can turn them around.
Read Story